What is mean by hacking devices?
Hello everyone, Welcomes to The Hackerzspot. Hacking devices are a device which was scripted by hackers to hack and extract data/information from victim web applications, computer systems, and phones. they are many types of hacking devices used by hackers for a different purpose. I am listing some of the hacking devices for you.
NOTE:-This is only for educational purposes. Don't use this for any illegal activities.
A Lan turtle is a hacking device used for administrative purposes mainly in offices namely IT companies to watch/surveillance the employee's computer systems and also act as a penetration testing tool providing stealth remote access, network intelligence gathering, and man-in-the-middle surveillance capabilities through a simple graphic shell.
2.Raspberry pi
Raspberry pi is a very low-cost credit card size computer. we only have to plug the monitor, keyboard, and mouse with that small-size computer. For hackers also it is a hacking device to hack with the help of installing the Kali Linux operating system at raspberry pi. And the major advantage of the raspberry pi is the size of the computer. It is very small so the hackers can carry it out easily as a hacking device.
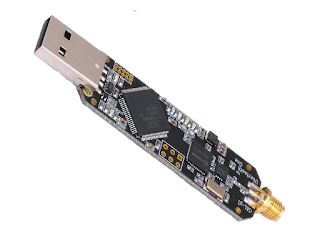
3.Rubber ducky USB
Rubber ducky is a hacking device that similarly appears like a Pendrive. The hackers script the Rubber ducky with malicious code to change it into a hacking device. By using this rubber ducky hackers can do different types of attacks also can steal the information of victims, install malware on computer systems without trapped by antivirus.
4.Ubertooth one
Ubertooth one is a hacking device it is an open-source Bluetooth test tool.we can able to a man-in-the-middle attack by using this Ubertooth one. when there are 2 devices sharing their data through Bluetooth, then hackers easily steal the data with Ubertooth one device with a man-in-the-middle attack.
5.Hardware keylogger
A hardware keylogger is a hacking device that similar to a rubber ducky USB. But the major difference between both is rubber ducky USB is scripted by a hacker for various purposes of hacking and the hardware keylogger is works for only one purpose keystroke logging. It is used to capture data that have we typed in our computer systems namely usernames, passwords, and confidential data.
Final words
I hope this post is helpful to you. If you facing any trouble comment below and also try all these hacking devices. thanks for visiting💓







nice post
ReplyDeleteJava institute in hyderabad